Background
For those unfamiliar, DLsite is a platform for the sale and distribution of primarily 2D Japanese games, both indie and commercial. It’s fairly easy to use, and for a foreigner is often cheaper than getting a physical copy since you avoid the fairly expensive shipping fees.
Anyway, a while back I preordered a physical copy of the game Rewrite+ (which was a mistake, but I digress). When the box arrived, I opened it to find a variety of goodies, including the expected game CDs. However, much to my surprise, a DLsite download code was also buried in there, right next to some useless crap like Weiβ Schwarz cards. This was completely unexpected, given that a download edition of the game wasn’t (and at the time of writing, still isn’t) available for sale anywhere, including DLsite.

I ended up redeeming the code, and after downloading the online version, found it was protected with a then-unfamiliar DRM scheme known as PlayDRM. PlayDRM was unveiled and made available for commercial titles at a conference celebrating DLsite’s 20th anniversary. It’s DLsite’s new in-house DRM solution, supposedly focused on “copyright management” (著作権管理) rather than “piracy prevention” (違法コピー防止). It is, again supposedly, intended for use with their upcoming game rental service, set to debut in spring of 2017. This service would allow consumers to purchase access to the game for a limited amount of time, and then at the end to optionally pay for the full game, minus the cost of the rental. Whether or not their earlier claims hold up with its usage in the case of Rewrite+ before the rental service has even launched is questionable at best.
Usage
For this section, I’m going to be talking about (and showing examples of) Rewrite+.
On the same page where you download the game files, the serial number is also listed.
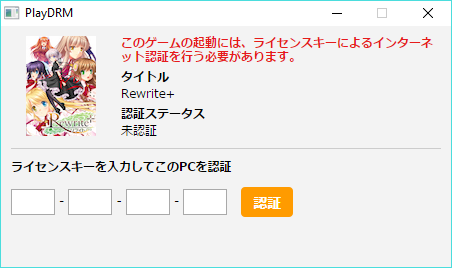
Once you’ve downloaded, combined, decompressed, and installed the game files, attempting to run the main game produces a dialog prompting for a license key. It’s worth noting that you must have internet access during this step for reasons explained later. Upon entering the key, the game is launched. In the particular case of Rewrite+, Visualarts are xenophobic assholes and have an additional measure taken against the main exe that prevents it from running unless you’re on Japanese Windows set to the proper timezone. They do this on all their games, however, and it’s not the focus of this post however annoying it may be.
Under the hood
So that’s a brief overview of the DRM. Of more interest, I think, is how it works, and some of the issues I have with how they’ve approached it.
File structure
It appears that after PlayDRM has been applied, a new executable with the name of the original is created to serve as a launcher. The original files are moved into a data directory, along with a modified version of the original executable, still with its original name.
Launcher
The new launcher executable appears to be built on NW.js. For those unfamiliar, you can think of it as essentially a minimal browser running node.js inside, letting you load up webpages as a standalone application. Unfortunately, this means that something as simple as displaying a login prompt and writing a file to disc requires an extra 65MB of storage space.
The one nice thing about this is it means you can very easily check out what it’s doing since it’s just a webpage and some javascript files (which they were kind enough to not even minify!). This also means they left in some amusing comments like “ハードウェアIDの取得にまれに失敗することがあるため、3回試行する” (roughly: “since fetching the hardware ID occasionally fails, it tries three times”). The whole thing has a bunch of fairly ghetto code, including gems like magic strings.
Anyway, once you run the launcher a few hundred lines of javascript are executed. The first thing it does is generate a 20-character hardware id by calling an embedded application, Phdid.exe. This application is packed and protected with Enigma Protector, which works similarly to VMProtect, which is more well-known. Amusingly, as far as I can tell a lot of Enigma Protector’s usage comes from pirates.
Then, it checks whether or not there is an existing license key, either in the registry or in appdata depending on the config (package.json inside the launcher exe). In Rewrite+’s case, it was at %appdata%\PlayDRM\key\rewrite_plus\reg.dat.
Sample file:
[Registration information]
License=G37VDVDFQQAWPLJVS
Name=PlayDRM
Key=XZ8RTAHIR2NRN327SL3P4SVW7A0HI1V9FMJFSFIAATHNC8701EMCQEWOR0UE8X03VI0S3MT25RVAT6VCAWVB7WAOANI7HAL
Path=Q:\Games\Key\REWRITE_DL\Rewrite_plus_PlayDRM\Rewrite_plus_DL版\StartData\GameData\SiglusEngine.exe
If you don’t have a registration file, it launches a small dialog to collect either a license key or your DLsite credentials, depending again on the config. DLsite claims the only method they use is the license key, though clearly they had the other functionality coded in as an option they could easily avail themselves of. After you enter the key, it sends a POST request to https://play.dlsite.com/api/playdrm/registration containing the “license id” (for example, ‘key.rewrite_plus’), your license key, your hardware id, your hostname, and a bunch of fun system info! This includes:
- Hostname
- Operating system name, platform, and version
- System uptime
- Total system memory
- Free system memory
- CPU cores
- List of drives
- User agent
- Screen size and color depth
I can’t think of a legitimate reason for them wanting this information (it’s not all used in generating the hardware id, I can assure you) other than gathering a bunch of (quite possibly not anonymous) user data without consent. Yippie!
Anyway, the request returns the license key, registration name, and registration key, all of which are written to the config file.
The launcher then checks the config as to whether or not the game requires online access at startup. If it does, it sends a GET request to the aforementioned registration url with your license key, getting back a list of valid hardware ids. If one of them matches yours, it continues. Obviously if verification isn’t required, that step is skipped. Rewrite+ did not require this. My guess is that this is how they plan to support rentals; once the rental period is over they’ll invalidate your hardware id and the launch process will end here.
Finally, it launches the main application itself, setting the working directory to that of the file.
Main executable
The main executable is protected with Enigma Protector, and after launch verifies the registration key based on the license key and your hardware id. In an effort to prevent easy creation of keygens, I won’t be discussing this step in detail, and thus it is left as an exercise for the reader.
Conclusion
So what do I think on all of this? For one, using NW.js for this is dumb as shit. For what they’re doing, there’s absolutely no need for all that space. It makes the user experience less pleasant and drives up DLsite’s bandwidth usage. Using Enigma Protector is also kinda dumb, though I guess it’s functional enough and probably cheaper than some of the alternatives.
Their data collection is a bit more concerning. It’s unnecessary, and their lack of disclosure leads me to suspect that it’s probably not anonymous, which is even worse! While I’d hope this isn’t present once they roll out the rental system, I kinda doubt it. We’ll see, I guess.
Finally, I hope they don’t require internet access at every startup should they continue to use this scheme for non-rental products. Being unable to play games on the go would be rather annoying.
Oh, I’m interested in checking out DMM’s scheme that they employed on Shinsou Noise to much public outcry. If I can get ahold of a full copy, I’d love to take a look. It apparently required people to download an extra 2GB of stuff, which is… interesting, to say the least.